A Comprehensive Guide to ISO 27001: Understanding and Achieving Information Security Excellence

What is ISO 27001? A Quick and Easy Explanation
ISO 27001 is an internationally recognized standard that provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. Developed by the International Organization for Standardization, this standard serves as a foundational framework that organizations can adopt to develop, implement, maintain, and continually improve an Information Security Management System (ISMS).
The primary aim of ISO 27001 is to help organizations protect their information in a methodical way. In the digital age, where data breaches and cyber threats are alarmingly prevalent, the importance of robust information security practices cannot be overstated. By following ISO 27001, companies not only mitigate risks related to information security but also reassure stakeholders that they are committed to safeguarding sensitive data.
ISO 27001 outlines a risk-based approach to identify potential security threats and establish adequate controls to address these risks. This involves conducting regular information security risk assessments, allowing organizations to evaluate their vulnerabilities and prioritize resources effectively. Importantly, it emphasizes continuous improvement, meaning that organizations must regularly review and update their security measures in response to evolving threats and technological advancements.
Implementing ISO 27001 can provide significant advantages, including enhanced reputation and customer confidence. Organizations that demonstrate compliance with this standard can showcase their commitment to information security, which can be a significant differentiator in competitive markets. Furthermore, achieving ISO 27001 certification can lead to improved operational efficiencies and reduction in costs associated with data breaches.
In summary, ISO 27001 is a vital standard for organizations aiming to establish a robust framework for information security, ensuring the protection of their critical data assets while adapting to the challenges of a transforming digital landscape.
Protecting Your Sensitive Information
In today’s digital landscape, protecting sensitive information has become paramount for organizations across various sectors. Sensitive information can include personal identifiable information (PII), financial records, intellectual property, and any confidential data that, if exposed, could harm individuals or businesses. Understanding the various forms of sensitive information and the risks associated with data breaches is essential in establishing effective information security measures.
The potential threats to sensitive information abound, ranging from cyberattacks such as phishing and malware to unintentional exposure through human error. These threats underscore the importance of having robust data protection strategies in place. A data breach can lead to significant financial losses, reputational damage, and legal repercussions for organizations. Furthermore, with regulations like GDPR and HIPAA mandating strict compliance to safeguard personal and sensitive data, the pressure on organizations to adopt comprehensive security frameworks is greater than ever.
ISO 27001 stands out as a vital framework that addresses these risks through a structured information security management system (ISMS). By adhering to ISO 27001 standards, organizations can identify the various forms of sensitive information they handle and assess the associated threats. The framework emphasizes risk assessment and management, enabling organizations to recognize vulnerabilities and implement necessary controls to mitigate potential data breaches effectively. Furthermore, ISO 27001 promotes a continuous improvement approach, ensuring that the security measures remain up-to-date with emerging threats.
Ultimately, adopting ISO 27001 empowers organizations to protect sensitive information systematically, fostering a culture of security awareness among employees. It equips them with the necessary tools to navigate the complexities of information security and safeguard against potential breaches. Thus, implementing these structured practices not only enhances the integrity and confidentiality of sensitive information but also reinforces trust with stakeholders and customers alike.
Key Components of ISO 27001
ISO 27001 is a comprehensive standard that delineates the requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). At the heart of this standard lies the ISMS framework, which serves as a structured approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. The ISMS framework is not merely a set of policies and procedures; it defines an organization’s commitment to information security by providing a systematic methodology for risk management and security control implementation.
Another critical component of ISO 27001 is the risk assessment and treatment processes. Organizations must assess their information security risks through a systematic identification of threats and vulnerabilities relevant to their specific context. This risk assessment helps organizations recognize where they are most vulnerable, allowing them to prioritize their resources effectively. Following the assessment, the risk treatment process enables organizations to select appropriate controls and actions to mitigate identified risks, ensuring that they are adequately protected.
Security controls form an integral part of ISO 27001. These controls are the actual measures taken to reduce risks to acceptable levels, encompassing a variety of technical, administrative, and physical safeguards tailored to the organization’s specific needs. By implementing these controls, organizations can create a robust information security strategy that aligns with their overall business objectives.
Finally, continual improvement is a cornerstone of ISO 27001. Rather than being a static process, an ISMS should evolve to adapt to new risks, technologies, and regulatory requirements. Organizations are encouraged to monitor and review their information security practices continuously and make adjustments as necessary. This dynamic approach not only enhances the effectiveness of security controls but also fosters a culture of information security awareness throughout the organization.
Benefits of Adopting ISO 27001
Implementing ISO 27001 provides organizations with a structured approach towards information security management, leading to numerous advantages. One of the foremost benefits is enhanced data security. Organizations that adhere to this international standard effectively identify and mitigate risks related to sensitive information. For instance, by following a risk assessment process outlined in ISO 27001, companies can proactively safeguard their data against unauthorized access, breaches, and cyber threats.
Another significant benefit of adopting ISO 27001 is the improved trust from customers and stakeholders. Organizations that demonstrate their commitment to data protection through ISO certification often gain a competitive edge. An example of this can be seen in the financial sector, where institutions that uphold stringent information security practices see increased client confidence, ultimately reinforcing their reputation in a competitive marketplace.
Moreover, compliance with legal requirements is a critical aspect of ISO 27001. The standard assists organizations in adhering to various data protection laws, such as the General Data Protection Regulation (GDPR). Engaging with ISO 27001 not only empowers organizations to navigate complex legal frameworks but also minimizes the risk of penalties associated with non-compliance.
Another notable advantage is the competitive advantage that ISO 27001 certification brings. Organizations can distinguish themselves by showcasing their dedication to information security. This certification often becomes a factor during the vendor selection process, as prospective clients prioritize working with partners that implement robust security measures.
Finally, ISO 27001 equips organizations with the capability to respond effectively to information security threats. The standard's implementation enables businesses to establish incident management protocols that ensure quick recovery and minimal impact during a security breach. Companies that have adopted the ISO 27001 framework are often better prepared to address security incidents swiftly, thereby reducing potential damages.
The ISO 27001 Certification Process
The ISO 27001 certification process is a critical pathway for organizations aiming to enhance their information security management systems (ISMS). Achieving this internationally recognized standard not only demonstrates a firm commitment to information security but also provides a competitive edge in the marketplace. As cyber threats continue to evolve, securing sensitive data is paramount, making ISO 27001 certification not just beneficial but essential for many businesses.
The certification journey typically starts with a gap analysis, where the organization evaluates its current ISMS against the requirements of ISO 27001. This analysis identifies potential weaknesses and areas where compliance is lacking, allowing businesses to develop a focused plan for implementation. Following this, organizations must establish an ISMS by defining their information security policies, setting objectives, and determining the scope of their ISMS based on their specific operational needs and risks.
Once the ISMS framework is established, the organization should conduct a risk assessment to identify potential threats to information assets, followed by implementing controls to mitigate identified risks. Documentation is equally vital; a comprehensive set of policies and procedures should be developed to ensure compliance with ISO 27001 requirements. This includes maintaining records of training, incidents, and management reviews.
After the implementation phase, a pre-assessment audit is often performed to verify the readiness for the formal audit. This audit helps in identifying any remaining gaps that need addressing. The final step is the certification audit conducted by an accredited external body. If the organization successfully meets the requirements, it will be awarded ISO 27001 certification, which must be maintained through regular surveillance audits. Overall, the ISO 27001 certification process, while rigorous, equips organizations with the tools needed to safeguard their information assets effectively.
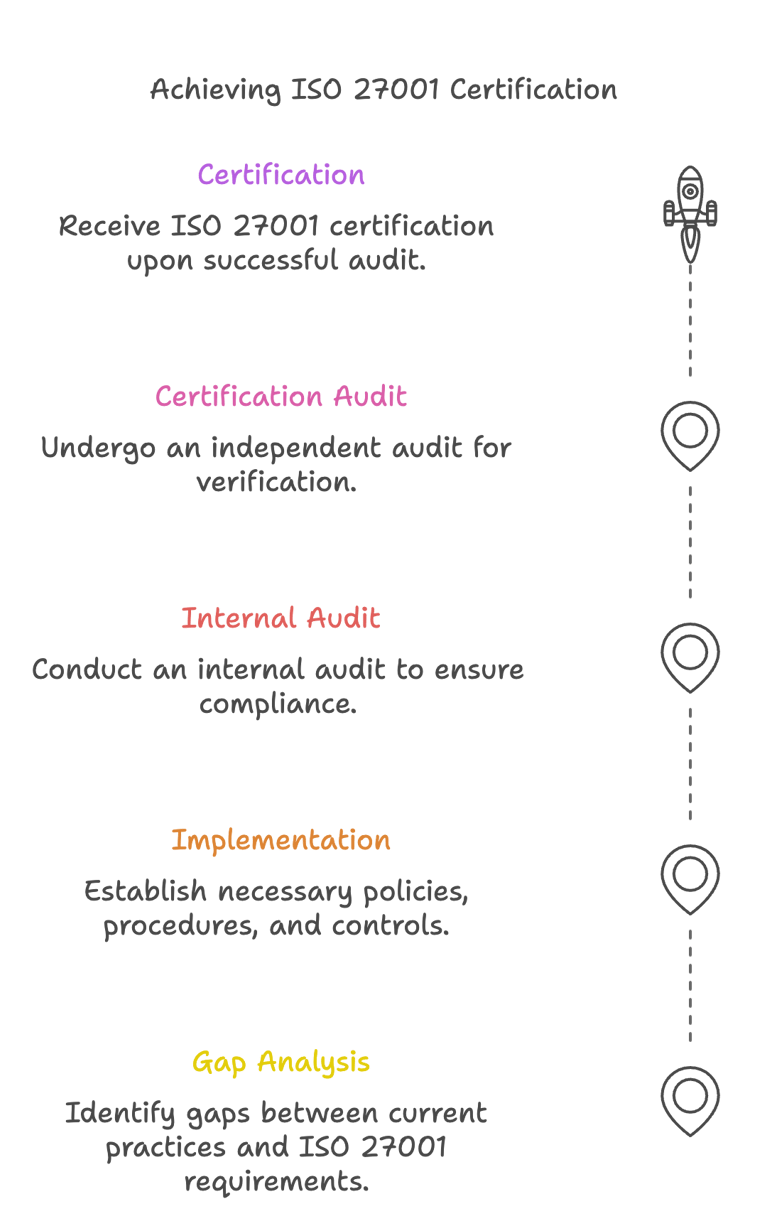
Getting Certified to ISO 27001 Involves the Following Steps
Achieving ISO 27001 certification is a structured process that organizations must carefully navigate to ensure their information security management system (ISMS) meets international standards. The journey to certification comprises five critical steps: gap analysis, implementation, internal audit, certification audit, and certification. Each of these steps plays a significant role in aligning an organization's practices with the requirements set forth by ISO 27001.
The first step, gap analysis, involves assessing the current information security practices against the ISO 27001 standards. This preliminary evaluation identifies areas where the organization falls short and highlights the necessary improvements needed to meet compliance. The insights gained during this phase are invaluable, as they direct the organization toward priorities for enhancing their information security protocols.
Following the gap analysis, the next step is implementation, which encompasses the development and execution of the ISMS. This step requires organizations to create policies and controls that address the recognized gaps in their current practices. Effective implementation is crucial, as it lays the groundwork for a sustainable information security framework that aligns with ISO 27001 requirements.
Once the ISMS is in place, an internal audit is conducted to ensure that all information security measures are functioning as intended. This independent assessment evaluates compliance with the established ISMS and identifies any weaknesses or areas for improvement before the external certification process begins.
After successful completion of the internal audit, organizations move on to the certification audit. During this step, an external auditor evaluates the ISMS against the ISO 27001 standards, determining whether the organization meets the required criteria for certification.
Finally, upon passing the certification audit, the organization receives its ISO 27001 certification, formally recognizing its commitment to information security excellence. Each of these five steps is integral to achieving ISO 27001 certification, ensuring that organizations not only comply with standards but also foster a robust culture of security.
ISO 27001 and ISO 27002
ISO 27001 and ISO 27002 are two pivotal standards within the ISO 27000 series, focusing on information security management. While both are integral to establishing a robust information security framework, they serve distinct purposes and functions. ISO 27001 lays out the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). In contrast, ISO 27002 provides a comprehensive set of guidelines intended to assist organizations in implementing and managing controls that can mitigate risks associated with sensitive information.
The primary distinction lies in their core focus: ISO 27001 outlines the necessary requirements for certification, allowing organizations to demonstrate compliance and effectiveness of their ISMS. This includes aspects such as risk assessment and treatment, leadership commitment, and maintaining adequate documentation. ISO 27002 complements this by detailing the necessary controls an organization may adopt to protect its information assets, essentially offering a toolkit for implementing the specifications detailed in ISO 27001. This guidance encompasses a wide range of practices concerning access control, asset management, and incident management, presenting best practices that can be tailored to the specific security needs of an organization.
The synergy between ISO 27001 and ISO 27002 is crucial in achieving optimal information security goals. While ISO 27001 provides the framework and requirements for certification, ISO 27002 equips organizations with the practical steps needed to implement the required controls effectively. Together, these standards promote a comprehensive approach to information security, enhancing the organization’s ability to manage threats and vulnerabilities in an ever-evolving digital landscape. Organizations seeking to bolster their security posture should prioritize a thorough understanding of both standards to maximize their effectiveness in information security management.
Making ISO 27001 Approachable
ISO 27001 can appear daunting, especially for small and medium-sized enterprises (SMEs) that may lack the resources of larger organizations. However, making this standard approachable is critical for achieving effective information security management. One of the first strategies involves breaking down the requirements of ISO 27001 into manageable components. Instead of trying to fulfill all aspects of the standard at once, SMEs can focus on key areas that align with their specific business context and risk profile. A phased approach allows organizations to gradually implement the necessary controls and policies, resulting in a more sustainable journey towards compliance.
Fostering a culture of security within the organization is another essential step. Engaging employees across all levels in discussions about the importance of information security can cultivate a collective sense of responsibility. Regular training sessions, workshops, and seminars should be organized to ensure that staff members are both informed about ISO 27001 requirements and empowered to contribute to the implementation efforts. This can also make the process less overwhelming, as the workforce will feel more involved and valued.
Additionally, SMEs should leverage available tools and resources to simplify the implementation process. There are numerous software solutions designed for managing compliance with ISO 27001, which can streamline documentation, risk assessments, and audits. Utilizing these tools not only reduces the administrative burden but also helps maintain transparency throughout the process. Lastly, considering external support from consultants or organizations with ISO 27001 expertise can provide guidance tailored to the specific needs and strengths of the SME, facilitating a smoother transition into compliance. By adopting these strategies, any organization can make ISO 27001 an attainable goal and secure its information environment more effectively.