ISO 27001: Practical Guide to Information Security Management in 2025
Introduction
ISO/IEC 27001:2022 is the internationally accepted benchmark for information security management. Used by global enterprises, critical infrastructure, and public agencies alike, it provides a structured, risk-driven approach for protecting sensitive data, processes, technology, suppliers, and staff. Today, regulators, clients, and business partners expect organizations to adopt its principles—making ISO 27001 not just a signal of seriousness about information security, but often a contractual or legal requirement.
Core Principles
Leadership Commitment and Governance
Effective security starts with strong, visible backing from senior management. ISO 27001 requires leadership to set explicit policies, allocate resources, and oversee ongoing improvement. A successful ISMS is never “just IT's job”—cross-department engagement is critical.
Scoped to Actual Business Risk
Organizations must carefully define the ISMS scope to include not only internal IT but also key business processes, third-party suppliers, cloud/adopted platforms, HR, and physical sites. A clearly scoped ISMS avoids both audit gaps and wasted effort.
Dynamic Risk Management
Risk assessment is the backbone of ISO 27001. Rather than generic checklists, organizations must identify their assets, understand threats and vulnerabilities, and prioritize risks according to real business impact. This assessment is living, not static—revisited as the threat landscape, technology stack, and regulations change.
Control Design and Implementation
Controls are chosen based on actual, prioritized business risks. ISO 27001’s supporting catalog (ISO 27002) lays out detailed technical, administrative, people, and physical controls—and now addresses modern threats including cyberattacks, supply chain compromise, remote work, and cloud computing. Policies and technical measures must be documented, tested in real workflows, and tailored beyond off-the-shelf templates.
Documentation and Audit Readiness
Practitioners must maintain practical, “living” documentation—policies, control listings, asset registers, risk treatment plans, incident logs, audit trails, and management review records. Internal audits test both formal compliance and operational reality; findings drive real process changes, not just paperwork.
Continual Improvement
The Plan-Do-Check-Act cycle is central. As the environment, business model, and regulations shift, organizations keep reviewing and adapting controls, policies, supplier contracts, and staff training. Stagnation is the top audit risk.
Updated Controls and Modern Threats
The 2022 updates bring major improvements:
· Control categories are simplified and mapped for easier ownership: organizational, people, physical, and technological.
· New and revised controls emphasize the real-world issues facing modern businesses—such as threat intelligence, secure configuration, software development security, data deletion/retention, and cloud service risk management.
· Each control now includes clear attributes, which assists with mapping to standards like GDPR or sectoral regulations, and supports transparent, measurable audits.
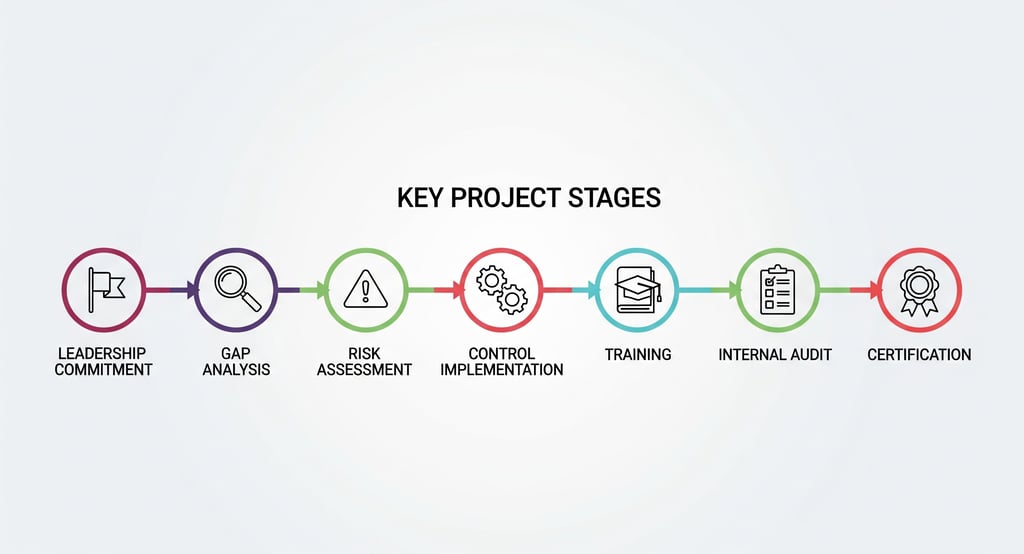
Practical Implementation Steps
1. Senior Leadership Buy-In
A successful ISMS only happens when executive management provides authority, budget, and visible oversight.
2. Gap Analysis and Scoped Planning
Map current state against the standard. Include all critical business units, IT infrastructure, suppliers, and relevant regulatory expectations. Define a realistic, sustainable scope.
3. Asset Inventory and Risk Assessment
Catalog digital, physical, and human assets. Perform threat modeling, document vulnerabilities, and classify risks by likelihood and impact.
4. Control Selection and Documentation
Implement technical and procedural controls tailored to risks and mapped to organizational workflows. Write policies that are practical—fit for purpose and updated as business needs evolve.
5. Training and Security Culture
Deliver ongoing, role-based awareness for all staff. Test incident response plans and readiness. Foster a culture where security is everyone’s responsibility.
6. Internal Audit and Management Reviews
Review documentation, technical controls, incident records, and user behavior. Use findings to refine the ISMS and drive measurable improvements.
7. Certification and Surveillance Audits
Undergo external audits for certification and ongoing verification. Maintain a living evidence base and demonstrate continual correction and improvement.
Audit Preparation
Auditors seek proof of:
· Senior management oversight
· Clear scoping and asset inventories
· Realistic risk assessments and updated risk treatment plans
· Policies, process flows, and operational logs
· Supplier, cloud, and third-party controls (contracts, SLAs, incident handling)
· Evidence of regular management reviews and action completion
Integration and Regulatory Alignment
Many organizations integrate their ISMS with other ISO standards (ISO 9001 for quality, ISO 22301 for business continuity) for unified governance. Regulatory overlap—such as GDPR, HIPAA, RBI guidelines—means your controls, contracts, and monitoring must satisfy multiple frameworks, and ISO 27001 provides a harmonized path.
Real-World Outcomes
Adopting ISO 27001 has enabled industry leaders in finance, healthcare, technology, and manufacturing to cut incidents, improve audit results, and earn client trust. Customer RFPs, regulatory scrutiny, and data privacy requirements increasingly reference the standard’s language and expectations.
Ongoing Challenges and Best Practices
Common pitfalls include:
· Under-scoping (ignoring suppliers or cloud)
· Over-scoping (trying to “boil the ocean”)
· Static risk registers and policies
· Security treated as an IT-only concern
· “Tickbox” training and incident drills
Leaders overcome these issues by embracing automation (GRC tools, compliance platforms), running cross-team simulations, and ensuring lessons from incidents truly drive adaptation and improvement.
Conclusion
ISO 27001 is a living, evolving management system. Its true value emerges when organizations move beyond checklists and engage strategically, operationally, and culturally—adapting continuously to new threats, technologies, and business realities. Built on rigorous standards, evidence-driven management, and broad engagement, ISO 27001 is the proven path to resilient, regulator-ready, and trust-building information security.
References
· ISO/IEC 27001:2022 Official Standard
https://www.iso.org/standard/27001
· ISO/IEC 27002:2022 Security Controls
https://www.iso.org/standard/75652.html
· ENISA Threat Landscape
https://www.enisa.europa.eu/topics/threat-risk-management/threats-and-trends/enisa-threat-landscape
· Reserve Bank of India Security Circulars
https://www.rbi.org.in/commonman/English/scripts/Notification.aspx
· ISACA Guide to ISO 27001 & 27002
https://www.isaca.org/resources/news-and-trends/newsletters/atisaca/2023/volume-7/a-guide-to-the-updated-iso-iec-27002-2022-standard-part-1
